A new intuitive report, that provides our Resellers detailed information on privileged accounts Multi-Factor Authentication (MFA) status for all customer Microsoft tenants that are using Azure Plan in Logicom Cloud Marketplace, in order to take action to have maximum MFA protection.
Requiring MFA for all privileged accounts makes it harder for attackers to access accounts. Administrative roles have higher permissions than typical users. If any of those accounts are compromised, critical devices and data is open to attack.
The report is available in Logicom Cloud Marketplace under:
Reporting -> Sales -> Microsoft Security Report
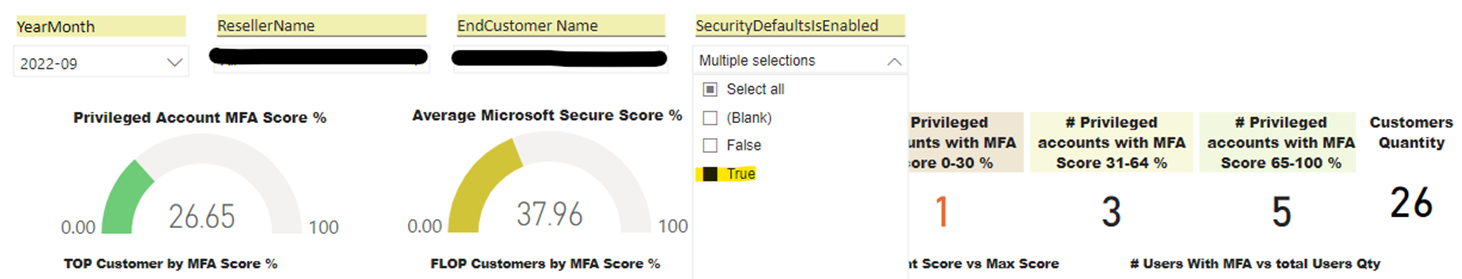
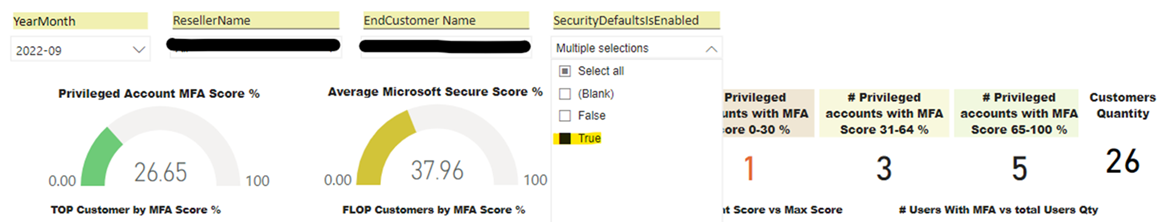
The Microsoft Security Report helps Resellers to:
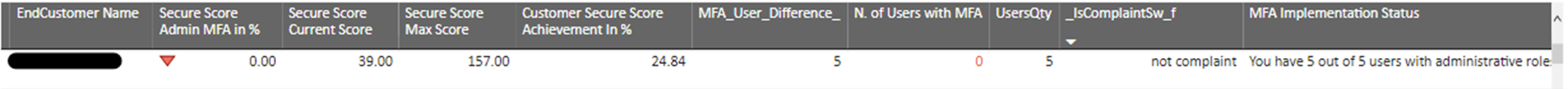
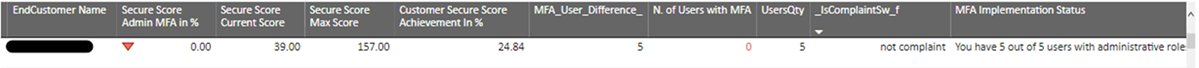
A “Privileged Account MFA %” score of 100% is given only when MFA is configured based on Microsoft recommendations. If only a subset of the total Privileged number of Privileged users are MFA protected, then a partial score is given. Below are some additional elements of the report:
The Microsoft Security Report in Logicom Cloud Marketplace includes all the information that each reseller needs to measure customers’ privileged accounts status in terms of MFA enablement and immediately plan MFA improvements. The report is updated at least three times a week to ensure that data is as current as possible.
More specifically this information can be easily accessed by the reseller as below: